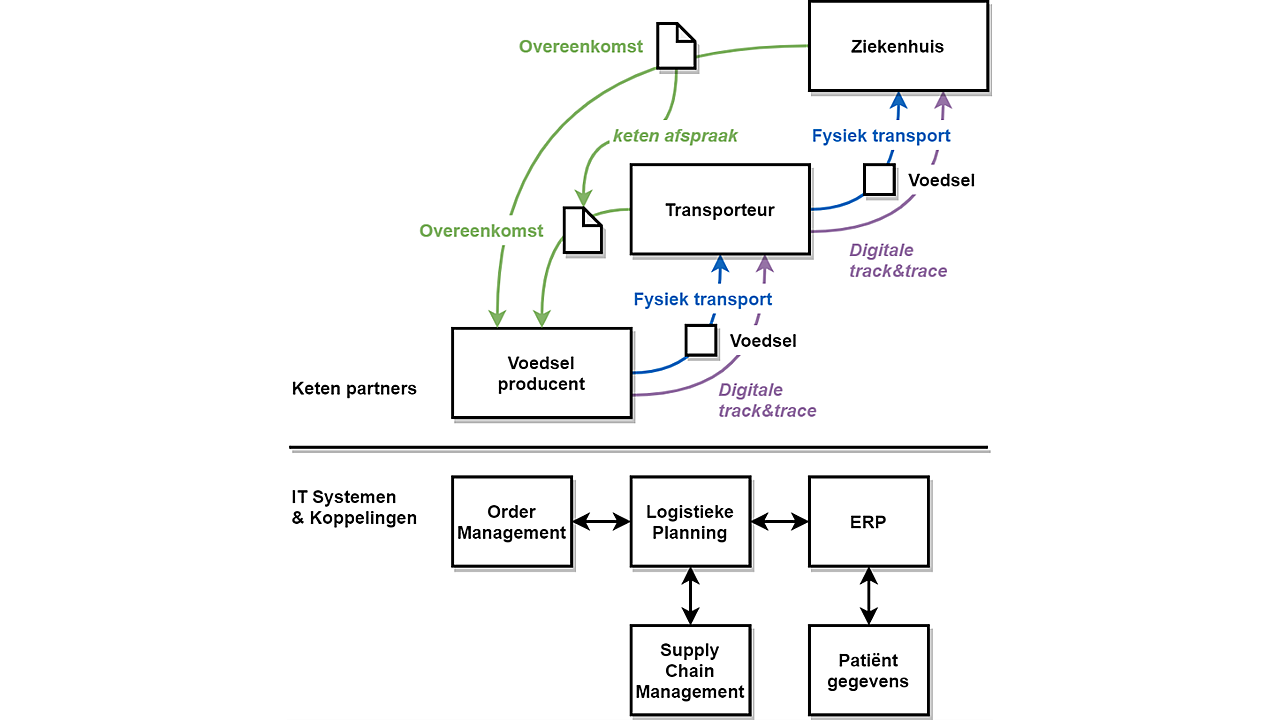
1. Specific vulnerabilities of suppliers and service providers: To make the supply chain NIS2-compliant, a risk assessment of the specific vulnerabilities of suppliers or service providers must be conducted. For example, in a hospital's case, what are the relevant/specific vulnerabilities of a transport company or food supplier? Similarly, the transport company will pose the same question to the food producer. In practice, it must be determined to what extent the respective company is classified as an NIS2 entity.
Interconnections between the IT systems of chain partners can be vulnerable. An attack on one component of the chain can have ripple effects. Among different domains, the most vulnerable systems must be protected extra diligently. For instance, an attack on a logistics partner's order management system should not pose an additional risk to a system containing sensitive patient data in a hospital.
2. Quality of products and services: In addition to assessing specific vulnerabilities, attention must be given to the quality of products and services from suppliers or service providers. One way to evaluate this is by examining the presence of certifications. It's worth mentioning the developments regarding the 'Cyber Resilience Act (CRA).' The CRA is a European proposal focusing on the digital security of products and services, already referencing NIS2 in various sections. Therefore, the assessment and certification of products and services must also be addressed separately. It's crucial to examine existing or forthcoming obligations or standards within a particular industry.
3. Secure development procedures for products and services: This topic closely relates to evaluating the security of products and services. NIS2 mandates that NIS2 entities consider digital security in the development of products and services when implementing security measures in the supply chain. This requires technical expertise for proper evaluation.
Specific attention is needed for periodically revising such evaluations. New threats may necessitate new measures. For instance, the increased threat of ransomware attacks has led to the deployment of new techniques such as ransomware-resistant 'immutable backup.' An agile and/or DevOps framework is necessary to implement such changes promptly. Periodically reviewing and adjusting these measures can become a crucial part of chain agreements.
Collaboration with customers and suppliers
This implies that NIS2 entities need to engage extensively with their customers and suppliers over their security in the coming year. However, it's not just about discussion; security must be assessed, and agreements on future assessments must be made. Otherwise, it's merely a snapshot, unlikely to be sufficient for NIS2 compliance.
Applied
The transport company, food producer, and hospital must engage in discussions about how their relationship is governed by everyone's cybersecurity obligations. Waiting is unwise because the contractual agreements made in the coming months must also comply with NIS2 obligations, both legally and technically, by October 17, 2024, eliminating any weak links in the supply chain.
More information (in Dutch):