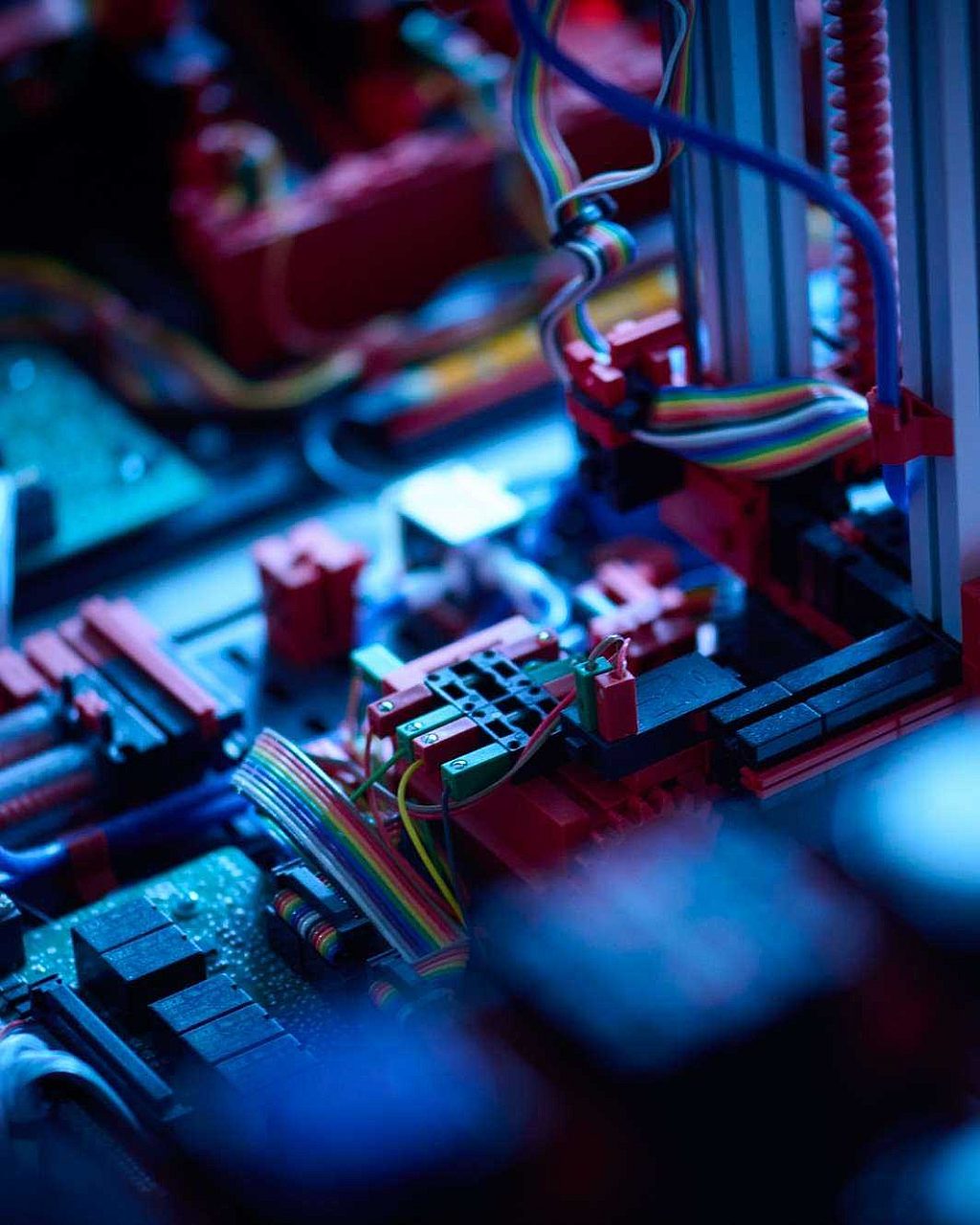
Onze verhalen

Schuberg Philis ranked Best IT company in The Netherlands
Annemieke Deering mrt. 03, 2025 en

Quantum Agility: preparing for a post-quantum world
Daan Stakenburg, Theodoor Scholte, Laurens Eversmann jul. 07, 2025 en

Engineering impact: how we built a business on Tech for Good
Aron van der Sanden, Maikel de Maertelaere, Ilja Heitlager, Agne Nainyte jul. 07, 2025 en

Building what matters: our vision on value-driven partnerships
Ilja Heitlager, Pleun de Goede jul. 07, 2025 en

The 90% behind AI: engineering for reliability
Julian Hessels, Jochem van Leeuwen, Anuschka Diderich jul. 07, 2025 en